Security Configuration
The following WAGO Solution Builder software components can communicate with on another securely, i.e., through encrypted communication, when configured accordingly:
- Web browser (with the WAGO Solution Builder software’s graphical user interface)
- WAGO Solution Builder server
- Device Communication Server
- PostgreSQL database server
This requires corresponding certificate files and correct configuration of the individual components. The installation process can optionally generate the initial setup for encrypted communication and appropriate certificates. These certificates are considered “temporary” and serve to illustrate functional certificate-based encryption.
The following certificates are generated during the installation process:
Certificate | Filename | Description |
|---|---|---|
1 | WAGO_Solution_Builder_Installer.pem | Private key and certificate of the “root CA” in one file |
2 | WAGO_Solution_Builder_Installer.crt | Certificate of the “root CA,” extracted from the .pem file |
3 | server.key | Private key of a server |
4 | server.crt | Certificate of a server |
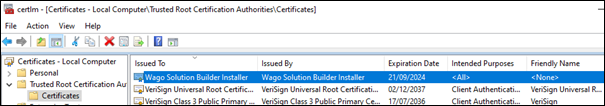
The files are stored in the C:\ProgramData\WAGO Software\WAGO Solution Builder\Certificates folder and used in the corresponding component configurations. The “root CA” certificate is automatically imported into Windows Certificate Manager as a “trusted certificate.” This is necessary in order for the server certificates that have been generated to be accepted in the components and the various browsers.
As soon as the WAGO Solution Builder software is put into productive use, public certificates provided by your company’s IT department should be used. In this productive environment, the following files are required (also see the table):
- WAGO_Solution_Builder_Installer.crt
- server.key
- server.crt
These three files must be copied to each server or physically present there. In addition, your IT department should ensure that you have trusted “root CA” certificates saved. For security reasons, the certificate imported during the installation process should be removed at the end.
Two alternatives exist for configuring a productive environment:
- Store the official certificate files in the certificate folder under the existing names. This requires no changes to the server configurations.
- Leave the names of the official certificate files as they are and adjust the file paths in the server configurations.
The possible server configurations are as follows:
Server | Path | Description |
|---|---|---|
WAGO Solution Builder | C:\ProgramData\WAGO Software\ WAGO Solution Builder\ WSB\Config\customSecurity.json | Replace “Path” and “KeyPath” with your own filenames. Here you can also set the URL where the WAGO Solution Builder software can be reached. The “Common Name (CN)” of the server certificate used must match the “SYSTEM USERNAME” in the PostgreSQL configuration. |
WAGO Device Communication Server | C:\ProgramData\WAGO Software\ WAGO Solution Builder\ DCS\Config\customSecurity.json | Replace “Path” and “KeyPath” with your own filenames. Here you can also set the URL where the WAGO Device Communication Service can be reached. |
WAGO Solution Builder PostgreSQL Database | C:\ProgramData\WAGO Software\ WAGO Solution Builder\ postgres\data\postgresql.conf | On the lines with ssl_ca_file, ssl_cert_file and ssl_key_file, replace the paths with you own filenames. |
C:\ProgramData\WAGO Software\ WAGO Solution Builder\ postgres\data\pg_ident.conf | The name under “SYSTEM USERNAME” corresponds to the “Common Name (CN)” of the accessing server certificate. This name must be identical to the WAGO Solution Builder software’s server certificate. The “localhost” row can be deleted. | |
C:\ProgramData\WAGO Software\ WAGO Solution Builder\ postgres\data\pg_hba.conf | This defines the access types. The line of type “hostssl” is relevant for encrypted access. The remaining lines are for local access with password protection. These lines can also be deleted if necessary. |
Every time a change is made, the corresponding service must be restarted. To do so, open the “Services” program and restart it.

Information on Secure Browser Access to the WAGO Solution Builder Software
The Edge and Chrome browsers use Windows Certificate Manager to verify a certificate without any further settings. In the Firefox browser, access to Windows Certificate Manager must be explicitly enabled. Every time a new certificate is installed, the Firefox browser must be restarted so a new “root CA” can be recognized.
Firefox configuration steps:
- Enter about:config in the address bar.
- A message appears describing possible risks; click the button to accept.
- In the “Filter” line, entersecurity.enterprise_roots.enabled.
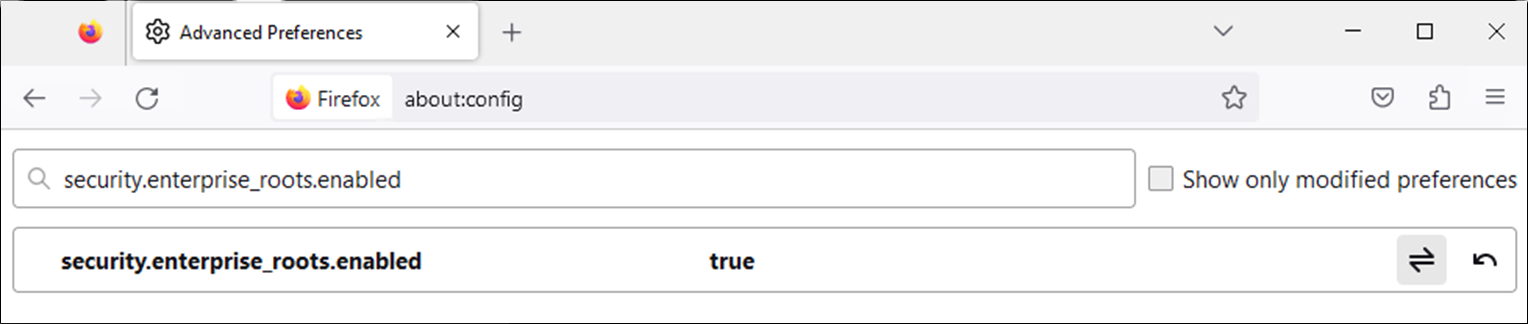
- Set the parameter to true.
- Restart.